QR Code Scams: How a Man Stole Money at a Petrol Pump Using a Fake Google Pay QR Code By: Javid Amin With the increasing use of digital payments, QR code scams have emerged as a new method of theft. Recently, a 23-year-old man from Mizoram, identified as H. Lalrohlua, was arrested for a scam involving QR codes at a petrol pump in Aizawl. By replacing the legitimate QR code sticker at the station with his own, he diverted customer payments directly to his account. The Incident at Mizofed Petrol…
Read MoreCategory: Technology
Technology
How a Man Lost ₹4 Lakhs in Minutes Trying to Book a Cab on Google: A Cautionary Tale of Online Scams
Beware: How a Simple Cab Booking Scam Cost a Man ₹4 Lakhs By: Javid Amin In today’s digital world, convenience is at our fingertips, but so too is risk. Recently, a resident of West Bengal fell victim to a sophisticated online scam while attempting to book transportation in Udupi, Karnataka, losing ₹4.1 lakhs in a matter of minutes. The unfortunate incident sheds light on the alarming tactics fraudsters use to exploit unsuspecting internet users. The Price of Convenience: A Costly Mistake in Cab Booking While searching for a car rental…
Read MoreMicrosoft Products Under Threat: Urgent Security Advisory Issued by CERT-In
Govt Issues Urgent Warning for Microsoft Windows Users: Check Critical Vulnerabilities Discovered in MS Products By: Javid Amin The Indian Computer Emergency Response Team (CERT- In) has issued an urgent advisory regarding multiple vulnerabilities found in Microsoft products. These vulnerabilities pose significant security risks, potentially allowing attackers to gain elevated privileges, bypass security restrictions, and access sensitive information. Users are strongly advised to apply appropriate security updates to mitigate these risks. Overview of Vulnerabilities CERT-In reported vulnerabilities in several Microsoft products, including Microsoft Windows, Microsoft Office, Microsoft Azure, Developer Tools, and Microsoft…
Read MoreProtect Your Phone, Protect Your Life: Top Security Tips for Digital Safety
Your Smartphone—A Gateway to Your Life By: Javid Amin In an era where our smartphones hold the key to so much of our daily lives, from banking to personal communications and everything in between, their security has never been more critical. A mobile device is now much more than just a communication tool; it’s a portal to your personal data, financial records, and even health information. As cyber threats become more sophisticated, it’s crucial to understand how to safeguard your device from these evolving dangers. This article provides a comprehensive…
Read MoreUnmasking Festive Frauds: Clone Sites Defraud Online Shoppers and Steal Personal Data
Festive Scams: How Clone Sites Are Preying on Shoppers This Season By: Javid Amin As festive sales go live across major e-commerce platforms in India, buyers are flocking to online stores like Flipkart to score significant deals on a range of products. However, not all that glitters is gold. Recent reports reveal that several clone websites are impersonating popular e-commerce platforms like Flipkart, drawing in unsuspecting customers with unbelievably low prices on premium products. These malicious sites exploit the high demand for discounted goods, often advertising high-end Apple iPhones for…
Read MoreShielding Your Digital Fortress: A Comprehensive Guide to Virus Protection
How to Protect Your Devices from Virus Attacks: A Comprehensive Guide By: Javid Amin In today’s digital age, our reliance on devices like computers, smartphones, and tablets has become an integral part of our personal and professional lives. From storing important documents to handling financial transactions, our devices are central to our daily routines. However, with this growing dependence comes an equally significant threat—viruses and other types of malware that can infect your devices, disrupt your systems, steal your data, and even compromise your privacy. While technology has advanced to…
Read MoreThe Dark Art of Phishing: A Closer Look at Social Engineering Tactics
Phishing: The Sneaky Art of Social Engineering By: Javid Amin In the intricate tapestry of the digital world, phishing stands out as a particularly insidious threat. It’s not a new concept, but its sophistication and frequency have evolved dramatically in recent years. Phishing attacks, in essence, are a form of social engineering, a technique that manipulates individuals into revealing sensitive information or performing actions that benefit the attacker. Understanding the Phishing Game At its core, a phishing attack involves a carefully crafted email or message designed to deceive the recipient.…
Read MoreUnderstanding Click Fraud: A Deep Dive into Types, Prevention, and Mitigation Strategies
Beyond the Click: Unraveling the Mystery of Click Fraud By: Javid Amin Click fraud, a pervasive threat in the digital advertising landscape, has become a significant concern for businesses worldwide. This deceptive practice, involving the artificial inflation of click counts on online ads, can lead to substantial financial losses and tarnish brand reputation. To effectively combat click fraud, it is essential to understand its various forms, the potential impacts, and the strategies to prevent and mitigate its occurrence. What is Click Fraud? Click fraud is a malicious act where individuals,…
Read MoreThe iPhone 16 Series: A Leap Forward in Smartphone Technology
Power, Performance, and Privacy: The iPhone 16 Series By: Javid Amin Apple has once again set the tech world abuzz with the launch of its highly anticipated iPhone 16 series. With four powerful models to choose from—the iPhone 16, iPhone 16 Plus, iPhone 16 Pro, and iPhone 16 Pro Max—the series continues to uphold Apple’s legacy of cutting-edge technology, elegant design, and performance-driven innovation. This new series introduces several groundbreaking features that make it stand out in an ever-competitive smartphone market. Whether you are a tech enthusiast, a photography fanatic,…
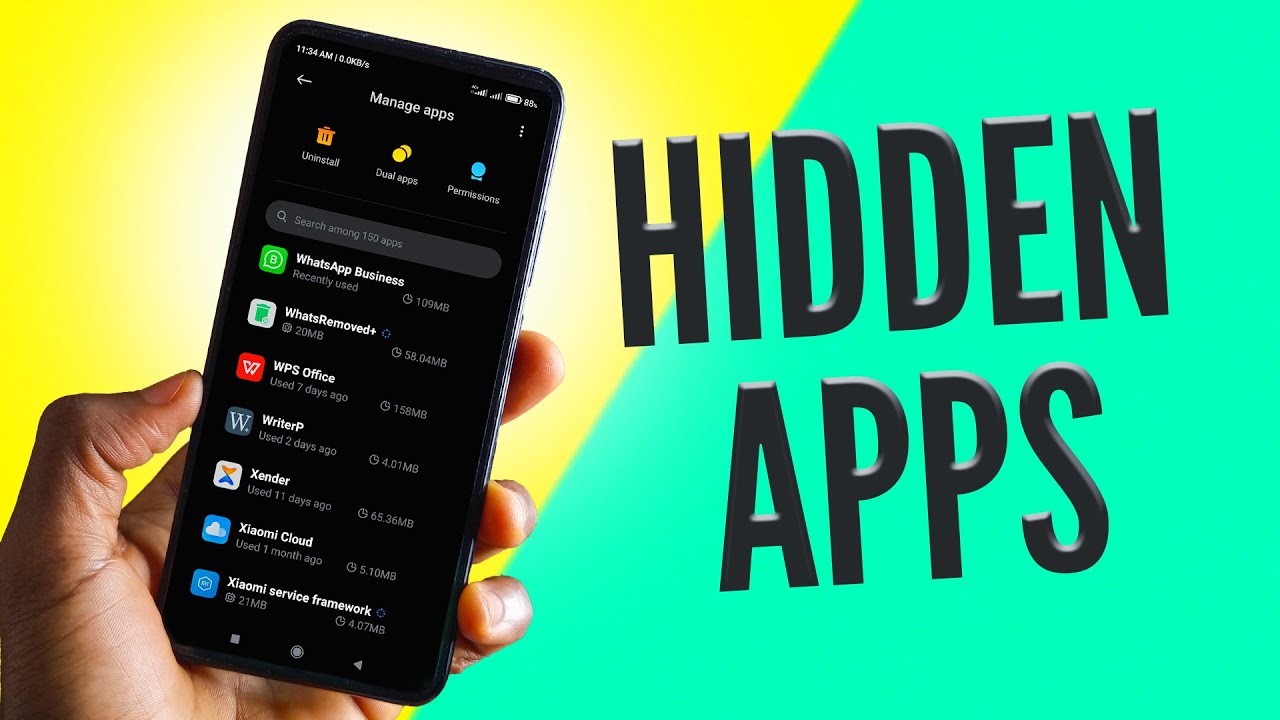
Read MoreDigital Detectives: Hunting Down Hidden Apps on Your Smartphone
Unmasking the Hidden Apps on Your Smartphone: A Comprehensive Guide By: Javid Amin The digital landscape is filled with apps, each promising to enhance our lives in some way. But what about the apps we don’t see? Hidden apps, those tucked away in the corners of our smartphones, can be a source of curiosity, concern, or even confusion. Let’s shed light on these digital enigmas. The Myth of Hidden Apps Contrary to popular belief, smartphones don’t harbor secret compartments for clandestine apps. However, the way operating systems like iOS and…
Read More