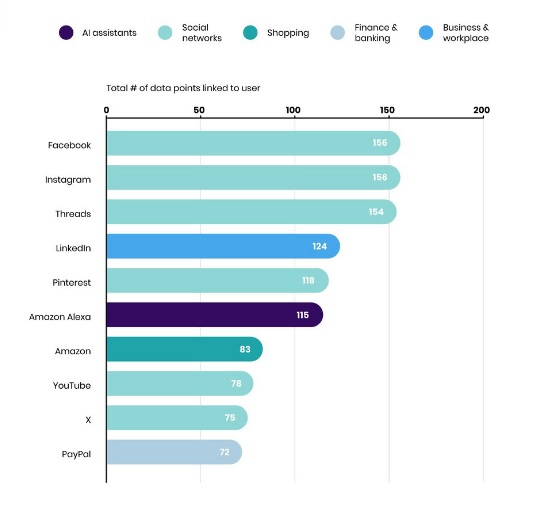
Top 10 Data Hungry Apps 2025 | Who Collects Your Sensitive Personal Data? | Privacy Report By: Javid Amin | Srinagar | 30 June 2025 The Constant Companion – Data Collection We live intertwined with our devices. The apps we use – to connect, shop, learn, navigate, and entertain ourselves – are indispensable tools of modern life. Yet, this convenience carries a hidden, often staggering cost: the relentless, often opaque, harvesting of our most sensitive personal information. It’s not a new concern, but the scale, sophistication, and sheer volume of data collection…
Read MoreCategory: Technology
Technology
The Geopolitical Ripple Effect: How Global Conflict is Reshaping India’s Workplace Landscape
War Impact on Indian Jobs: 63% Hiring Freeze, Salary Cuts & Workforce Anxiety | Deep Analysis By: Javid Amin | 23 June 205 When Distant Wars Hit Home The smoke rising over Gaza and the rubble of Iranian nuclear facilities might seem worlds away from Bengaluru’s tech parks or Mumbai’s trading floors. Yet, a seismic shift is underway. As geopolitical fault lines fracture global stability, India’s economic resilience is being tested in an unexpected arena: its workplaces. A groundbreaking survey by Genius Consultants exposes the human cost of global conflict—63%…
Read MoreAI Prompting Tips That Work Everywhere: Expert-Approved Hacks for ChatGPT, Gemini, Claude & More
Global Prompting Power: AI Prompting Tips That Work on ChatGPT, Gemini, Claude & More By: Javid Amin | 20 June 2025 Artificial intelligence is transforming how people work, learn, and solve problems—not just in Silicon Valley but worldwide. Popular AI chatbots like ChatGPT (OpenAI), Gemini (Google), Claude (Anthropic), and Perplexity AI have become indispensable to professionals, students, teachers, marketers, and researchers from New York to Nairobi. As AI becomes more ubiquitous, the one thing users across continents quickly learn is this: your output is only as good as your input.…
Read MoreWoman Loses Rs 20 Crore in Aadhaar Digital Arrest Scam: Why Do People Keep Falling for These Traps?
A Shocking Scam That Cost an Elderly Woman Rs 20 Crore By: Javid Amin In a shocking cybercrime case, an 86-year-old woman from Mumbai fell victim to fraudsters impersonating police officers, losing over ₹20 crore in an Aadhaar digital arrest scam. Between December 26, 2024, and March 3, 2025, scammers manipulated her into believing that her Aadhaar card had been misused in a serious criminal case. Under immense psychological pressure and fear of legal action against herself and her family, she was coerced into transferring huge sums of money to…
Read MoreBeware of Online Scams: Woman Loses Rs 1.2 Crore in Investment Fraud
Online Investment Scam: A Cautionary Tale for Digital Investors By: Javid Amin In an era of increasing online fraud, a 61-year-old government official from Shahdara fell victim to a sophisticated investment scam, losing a staggering Rs 1.2 crore to fraudsters. The scammers, posing as representatives of a fake UK-based online shopping platform, lured her with the promise of high returns. Over 78 days, she was manipulated into investing her life savings, only to realize too late that it was a trap. The Anatomy of the Scam: How It Unfolded The…
Read MoreFrom Malicious Downloads to Empty Bank Accounts: Anatomy of a ₹2.8 Crore Heist & Expert Tactics to Outsmart Digital Fraudsters
A Digital Heist in India’s Silicon Valley By: Javid Amin Bengaluru, India’s tech capital, is now the battleground for a sinister cybercrime wave. In January 2025, 42-year-old Hari Krishnan became the latest victim of a ruthless scam involving fake traffic challans, malicious APK files, and orchestrated financial theft. This incident isn’t isolated—it’s part of a sophisticated criminal playbook exploiting trust in authority, tech illiteracy, and gaps in India’s cybersecurity infrastructure. Here’s a deep dive into how these scams work, why they’re escalating, and how to armor yourself against digital predators.…
Read MoreDon’t Be a Victim: Top Android Security Tips You Need to Know
How to Secure Your Android Phone from Hackers and Scammers By: Javid Amin In today’s hyper-connected world, smartphones are more than just communication tools—they’re our lifelines, housing everything from personal photos to sensitive financial information. Unfortunately, this makes them prime targets for hackers and scammers. If you’re an Android user, staying a step ahead of cybercriminals is essential. Here’s your comprehensive guide to securing your Android phone and safeguarding your digital life. Why Android Security Matters With Android being one of the most widely used operating systems globally, it’s no…
Read MoreYour iPhones and Android Smartphones Are at Risk: Five New Pegasus Spyware Variants Discovered
Newly Discovered Pegasus Spyware Threats Put iPhones and Android Devices at Risk By: Javid Amin In a groundbreaking discovery, mobile security firm iVerify has unveiled five previously undetected Pegasus spyware variants targeting both iPhones and Android devices. This revelation underscores a growing threat: spyware once reserved for high-profile individuals is now being used to infiltrate the smartphones of ordinary citizens. The findings highlight an urgent need for enhanced mobile security as Pegasus continues to evolve and evade traditional defenses. What is Pegasus Spyware and Why Should You Care? Developed by…
Read MoreLessons from a ₹1.7 Crore Mistake: Protect Yourself from Cyber Scams
Beware of Digital Deception: Karnataka Man Duped of ₹1.7 Crore by Fake CBI and TRAI Officials By: Javid Amin In today’s digital age, online scams have reached alarming levels of sophistication. The recent case of a Karnataka resident losing ₹1.7 crore to fraudsters posing as officials from the Central Bureau of Investigation (CBI) and the Telecom Regulatory Authority of India (TRAI) is a stark reminder of the need for heightened vigilance. This shocking scam, reported on November 11, unveils the extent to which criminals go to exploit fear and manipulate…
Read MoreThe Hidden Danger of QR Codes: How Scammers Use Technology to Steal Your Money
QR Code Scams: How a Man Stole Money at a Petrol Pump Using a Fake Google Pay QR Code By: Javid Amin With the increasing use of digital payments, QR code scams have emerged as a new method of theft. Recently, a 23-year-old man from Mizoram, identified as H. Lalrohlua, was arrested for a scam involving QR codes at a petrol pump in Aizawl. By replacing the legitimate QR code sticker at the station with his own, he diverted customer payments directly to his account. The Incident at Mizofed Petrol…
Read More