Top 10 Data Hungry Apps 2025 | Who Collects Your Sensitive Personal Data? | Privacy Report
By: Javid Amin | Srinagar | 30 June 2025
The Constant Companion – Data Collection
We live intertwined with our devices. The apps we use – to connect, shop, learn, navigate, and entertain ourselves – are indispensable tools of modern life. Yet, this convenience carries a hidden, often staggering cost: the relentless, often opaque, harvesting of our most sensitive personal information. It’s not a new concern, but the scale, sophistication, and sheer volume of data collection continue to escalate, often far beyond what users consciously permit or even comprehend.
The phrase “if you’re not paying for the product, you are the product” has become a weary cliché, but its truth resonates more profoundly than ever. A landmark 2025 study by research firm Apteco, focusing specifically on “Data Linked to You” within Apple’s privacy label ecosystem, has cast a stark, data-driven light on this reality. Their findings confirm what privacy advocates have long suspected: social media platforms are the undisputed champions of data extraction, with Meta’s empire leading the charge.
But this isn’t just about knowing your name or email. The depth and breadth of information collected paints an incredibly intimate portrait – a “digital fingerprint” – encompassing your location history, physical characteristics, financial habits, deepest interests, social connections, and even subtle behavioral patterns. This report isn’t merely a list; it’s a crucial map revealing the contours of the invisible landscape where our personal data is the most valuable currency. Understanding who collects what, why it matters, and crucially, how you can regain some control, is no longer optional; it’s fundamental digital self-defense.
Decoding “Data Linked to You”: What Apple’s Labels Really Reveal
Before diving into the culprits, it’s vital to understand the lens through which Apteco conducted its research: Apple’s App Privacy Labels. Introduced in late 2020, these labels were a significant step towards transparency, forcing developers to self-report the types of data their apps collect and whether that data is “Linked to You” (directly tied to your identity via identifiers like your Apple ID, phone number, or email) or “Used to Track You” (shared with third parties for advertising or data brokerage).
Apteco’s study zeroed in on “Data Linked to You” – the most sensitive category. This isn’t anonymized, aggregated data. This is information that can be directly connected back to you, the individual user. Think of it as the difference between knowing “someone in ZIP code 90210 bought shoes” and knowing “John Smith at 123 Sunny Lane bought red Nike running shoes size 10 at 3:15 PM using his PayPal account linked to john.smith@email.com after searching for ‘best running shoes for flat feet’ on Google earlier that day.”
Here’s a breakdown of the key data types Apteco tracked, expanded with critical context often missing from simple labels:
-
Contact Information: Name, email, phone number, physical address.
-
Why Apps Want It: The bedrock of identity verification and cross-platform linking. Your phone number is a near-universal identifier. An address allows for hyper-local targeting (think: ads for nearby stores, real estate valuations, insurance risk profiling).
-
Beyond the Obvious: This data is used to build your core profile and link your activity across different services owned by the same company (e.g., Facebook and Instagram) or shared with partners.
-
-
Identifiers: User ID, Device ID (like IDFA or AAID), Advertising ID.
-
Why Apps Want It: These are the unique digital license plates assigned to you or your device. They are essential for tracking your activity across apps and websites, building long-term behavioral profiles, and targeting ads. Resetting your Advertising ID helps, but persistent identifiers can often be re-linked.
-
Beyond the Obvious: Even if you use a pseudonym, these identifiers ensure your activity is consistently attributed to “User X” profile. They form the backbone of the ad tech ecosystem.
-
-
Usage Data: Product interaction, advertising data, other usage data.
-
Why Apps Want It: This is the goldmine of how you behave. Every tap, scroll, pause, like, share, video watched (and for how long), ad clicked (or skipped), feature used – it’s all meticulously logged.
-
Beyond the Obvious: Algorithms analyze this to predict your future behavior, manipulate your feed for maximum engagement (and ad views), identify your mood or interests at specific times, and refine their models. It’s not just what you do, but how you do it.
-
-
Diagnostics: Crash data, performance data, other diagnostic data.
-
Why Apps Want It: Primarily for improving app stability and performance. Legitimate use.
-
Beyond the Obvious: Can sometimes include logs containing snippets of user activity or device state at the time of a crash. While usually anonymized, the potential for linkage exists in complex systems.
-
-
Location: Precise Location, Coarse Location.
-
Why Apps Want It: Possibly the most sensitive category after identifiers. Precise location (GPS-level) reveals your exact whereabouts in real-time. Coarse location (based on IP or cell towers) gives a broader area (like city or neighborhood).
-
Beyond the Obvious: Location history builds patterns: home, work, gym, doctor’s office, places of worship, political rallies, nightlife spots. This enables geofencing (triggering ads when you enter a specific area), location-based content, and deep insights into lifestyle, habits, health inferences, and socioeconomic status. “Only While Using” is crucial, but many apps push for “Always.”
-
-
Contacts: Your entire address book.
-
Why Apps Want It: To rapidly build your social graph – “find friends” features are the common justification. This massively accelerates network growth for the platform.
-
Beyond the Obvious: Harvests contact details (names, numbers, emails) of people who haven’t even signed up for the app, violating their privacy by proxy. Used for shadow profiling and understanding your real-world influence network.
-
-
User Content: Emails, text messages, photos, videos, audio data, gameplay content, customer support content, other user content.
-
Why Apps Want It: Photos/videos are analyzed by AI for objects, faces, locations, and even emotions. Audio recordings (voice messages, ambient sound for features like Facebook’s now-defunct Nearby Friends) can be processed. Emails/messages within the app are scanned for content, keywords, and sentiment (ostensibly for safety/features, but also for ad targeting).
-
Beyond the Obvious: This is direct access to your private communications and creative output. While platforms claim automated scanning, the potential for misuse or exposure in breaches is high. Deeply personal.
-
-
Search History: What you type into the app’s search bar.
-
Why Apps Want It: Reveals your immediate, often unfiltered interests, questions, and needs in real-time. Highly valuable for intent-based advertising.
-
Beyond the Obvious: Even searches you never act on are logged and analyzed, revealing hidden anxieties, curiosities, or plans.
-
-
Browsing History: Your activity within in-app browsers (like the one in Facebook or Instagram).
-
Why Apps Want It: Allows tracking of every website you visit without leaving their app, bypassing some traditional browser privacy controls. Captures detailed engagement with external content.
-
Beyond the Obvious: A major privacy loophole. Your activity on news sites, shopping sites, or sensitive health sites viewed within the app is fully visible to the platform.
-
-
Purchases: Transaction history, purchase history, financial info (if linked, like PayPal), payment info.
-
Why Apps Want It: Direct insight into your spending power, habits, brand loyalty, and life events (e.g., buying baby products, engagement rings). Used for highly targeted e-commerce advertising and creditworthiness profiling.
-
Beyond the Obvious: Even if you don’t link a payment method, tracking what you look at, add to cart, or wishlist provides strong purchase intent signals.
-
-
Sensitive Info: Racial or ethnic data, sexual orientation, health data, biometric data, religious beliefs, union membership, genetic data.
-
Why Apps Want It: While rarely collected explicitly via standard forms, this data is often powerfully inferred. Likes, groups joined, pages followed, location data (visiting a clinic), search history (“HIV symptoms”), photos (showing skin conditions), voice analysis (detecting illness), or even typing patterns can reveal these sensitive attributes.
-
Beyond the Obvious: Inferred sensitive information is still used for targeting and profiling, often without explicit consent. It carries significant risks for discrimination, manipulation, and harm if breached or misused.
-
-
Other Data: A catch-all category that can encompass a vast array of information like device characteristics (model, OS), connection type (Wi-Fi/cellular), installed apps, and more.
-
Why Apps Want It: Helps with app optimization but also builds a more complete device fingerprint, aiding tracking and profiling.
-
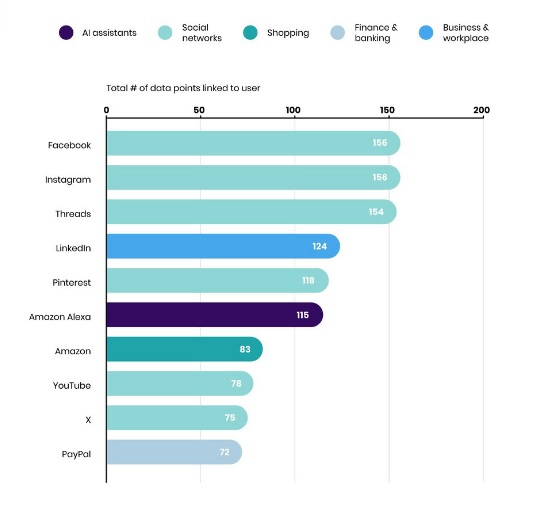
The Apteco Report: Unveiling the Top 10 Data Harvesters of 2025
Armed with this understanding of “Data Linked to You,” Apteco meticulously analyzed Apple’s privacy labels for thousands of popular apps. Their findings were unequivocal: Social Media apps are the undisputed data vacuum cleaners. The top 10 list is dominated by platforms whose business models fundamentally rely on knowing users intimately to fuel hyper-targeted advertising.
Here is the Apteco Top 10, dissected with the “why” and “how” behind their data hunger:
-
Facebook (Meta): The Data Leviathan
-
The Why: Facebook’s entire empire is built on advertising revenue fueled by unparalleled user profiling. Its core business is knowing everything about you to sell highly effective ad space.
-
The How: Collects virtually every category of “Data Linked to You” listed above at an industrial scale. From precise location tracking your movements, to scanning photos and messages (for content and faces), to logging every interaction, search, and click, to building exhaustive social graphs via contacts, to inferring sensitive traits. Its off-app tracking via pixels and SDKs embedded across the web extends its reach far beyond the app itself. It’s the blueprint for surveillance-based advertising.
-
-
Instagram (Meta): Visual Life = Data Goldmine
-
The Why: Owned by Meta, Instagram leverages the same ad infrastructure. Its focus on visual content provides uniquely rich data: what you see, for how long, what you create, who and what you find aesthetically pleasing.
-
The How: Tracks precise location (especially for Stories/Reels location tags), analyzes every photo/video uploaded (objects, faces, locations, text via OCR), logs extensive usage data (time spent, re-watches, explore tab clicks), DMs (content scanned), search history, contacts, browsing history within its in-app browser, and purchases made via shopping features. Deeply integrated with Facebook’s data ecosystem.
-
-
Threads (Meta): The Newcomer with Old Habits
-
The Why: Meta’s challenger to X (Twitter) inherits the parent company’s DNA. Rapid user growth is fueled by aggressive data collection to bootstrap its ad targeting capabilities quickly.
-
The How: Despite being text-centric initially, it collects a vast array: precise location, contacts (for finding connections), usage data (engagement with posts, topics), user content (posts, replies), search history, browsing history (via in-app browser), identifiers, and health/fitness data potentially inferred from activity or linked accounts. Its deep integration with Instagram facilitates immediate, rich profiling.
-
-
LinkedIn (Microsoft): Your Professional Persona Under the Microscope
-
The Why: While positioned as a professional network, LinkedIn is a powerhouse for B2B advertising and recruitment services. Understanding your career, skills, company, network, and professional interests is its core value proposition.
-
The How: Collects extensive contact info and employment history directly from your profile. Tracks your activity: who you view, what jobs you look at, what content you engage with, who you message. Uses precise location (for “Nearby” features and office location validation). Accesses contacts to expand your network. Analyzes messages and posts. Can infer salary brackets, career trajectory, and professional vulnerabilities.
-
-
Pinterest: The Aspirational Data Trap
-
The Why: A visual discovery engine heavily reliant on e-commerce partnerships and advertising. Knowing what you desire, plan (weddings, home renos, travel), or find inspiring is critical for converting pins into purchases.
-
The How: Tracks precise location (for local recommendations). Logs every pin saved, board created, search performed, ad clicked. Analyzes images pinned and uploaded. Uses contacts to find friends. Monitors browsing history within its in-app browser to see what products you look at elsewhere. Builds intricate interest profiles (“foodie,” “minimalist design lover,” “DIY enthusiast”).
-
-
Amazon Alexa: The Eavesdropping Ecosystem Hub
-
The Why: Alexa aims to be the central hub for your smart home and shopping. Voice interactions provide incredibly personal data, and its integration with Amazon’s retail empire creates a closed-loop data powerhouse.
-
The How: Collects and analyzes voice recordings and transcripts (core functionality, but stored and analyzed). Tracks precise location (for location-based requests/responses). Accesses contacts (for calling/messaging). Logs usage data (skills used, routines triggered). Integrates purchase history from Amazon. Knows your device usage patterns (when lights go on/off, when you’re home). Sensitive health data can be collected via health-related skills or devices. A constant, ambient data stream.
-
-
Amazon Shopping: The Everything Store Knows Everything
-
The Why: To dominate e-commerce through personalization, predictive shipping, and maximizing purchase frequency. Knowing what you buy, browse, wishlist, and even think about buying is key.
-
The How: Tracks precise location (for delivery, local store features). Logs exhaustive search and browsing history within the app. Records detailed purchase history. Uses identifiers to link activity across devices. Analyzes product views and time spent. Accesses contacts (for sharing lists/registries). Can infer health conditions (medical purchases), family status (baby products), hobbies, and financial situation.
-
-
YouTube (Google): Where Watching Means Being Watched
-
The Why: Google’s advertising model is built on data. YouTube, as the world’s largest video platform, captures immense attention and reveals deep interests, opinions, and even moods through viewing habits.
-
The How: Tracks precise location (for local content, ads). Logs every video watched, search made, comment posted, channel subscribed to, ad interaction. Analyzes watch time, re-watches, skips. Uses identifiers for cross-device tracking. Accesses contacts (for sharing videos). Builds sophisticated interest and demographic profiles. Can infer sensitive topics (mental health, political views) based on viewing history.
-
-
X (Formerly Twitter): The Real-Time Pulse & Data Stream
-
The Why: Despite ownership changes, X relies on advertising. Its value is in real-time conversation and trending topics, providing unique insights into current interests, news consumption, and public sentiment.
-
The How: Tracks precise location (for trends, location tagging). Logs tweets, DMs (content scanned), searches, accounts followed, topics engaged with, ads clicked. Uses identifiers for tracking. Accesses contacts (find friends). Monitors browsing history via in-app browser. Can infer political leanings, niche interests, and professional focus areas with high granularity based on who you follow and engage with.
-
-
PayPal: The Financial Data Custodian (with a Marketing Side Hustle)
-
The Why: Primarily needs data for fraud prevention and transaction processing. However, it increasingly leverages its vast financial dataset for targeted advertising and merchant services, blurring the lines.
-
The How: Collects full financial information (bank accounts, cards) and detailed transaction history. Tracks precise location (for fraud detection, local offers). Accesses contacts (for sending/receiving money). Logs usage data within the app. Can build comprehensive profiles of spending habits, income streams, donation patterns, and financial stability. While more regulated, the sensitivity of this data is extreme.
-
The Engine of Extraction: How Your Data Fuels the Machine
Understanding why these apps are so voracious requires peering into the engine room of the modern digital economy: Data Monetization.
-
Hyper-Targeted Advertising: The Primary Fuel
-
The Mechanism: Your collected data creates an incredibly detailed profile. Advertisers bid to show ads to specific segments: “Women aged 25-34, living in Seattle, interested in sustainable fashion and yoga, who recently searched for hiking boots, and have a household income >$100k.” The more precise the targeting, the higher the ad rates the platform can charge, and the more effective (and thus valuable) the ad space becomes.
-
The Depth: It goes beyond demographics. Platforms target based on predicted life events (moving, getting married, expecting a child), moods (inferred from activity patterns or content consumed), vulnerabilities (financial stress inferred from searches), and even personality traits. This is “surveillance capitalism” in action – modifying behavior at scale for profit.
-
-
Algorithmic Optimization: Keeping You Hooked
-
The Mechanism: Usage data feeds powerful AI algorithms (like Facebook’s or TikTok’s recommendation engines). These algorithms learn what content keeps you specifically scrolling, watching, or clicking. Every interaction is feedback, refining the feed to maximize your “Time Spent” – the core metric for ad exposure. This creates addictive loops and filter bubbles.
-
The Consequence: The app becomes incredibly engaging, but often at the cost of showing you diverse viewpoints or allowing disengagement. Your attention is the product being optimized for sale to advertisers.
-
-
Product Development & Personalization: The User Experience Facade
-
The Mechanism: Data informs new features and tailors the app experience. “People you may know,” personalized news feeds, location-based check-ins, product recommendations – all rely on harvested data.
-
The Double-Edged Sword: While this can enhance usability, it’s primarily driven by engagement and monetization goals, not purely user benefit. Features are designed to extract more data or create new advertising opportunities.
-
-
Data Brokerage & Partnerships: The Hidden Marketplace
-
The Mechanism: While major platforms like Meta and Google primarily use data internally for their own ad networks, many apps (especially smaller ones or those with SDKs) share or sell data to third-party data brokers. These brokers aggregate data from countless sources to build even more comprehensive profiles, which are then sold to advertisers, insurers, employers, or even political campaigns.
-
The Opacity: This secondary market is notoriously opaque. Users rarely know who ultimately accesses their aggregated data or for what purposes. “Other Data” categories in privacy policies often hide this sharing.
-
-
Credit Scoring & Risk Assessment: The Financial Implications
-
The Mechanism: Increasingly, non-traditional data – social media activity, purchase history, browsing habits – is being explored or used to assess creditworthiness, insurance risk, or employability. While sometimes framed as “financial inclusion,” it raises severe concerns about bias, accuracy, and lack of transparency or recourse.
-
The Risk: Being denied a loan or charged higher insurance premiums based on inferred data from your app usage, which may be inaccurate or discriminatory.
-
Beyond the Top 10: The Pervasive Ecosystem of Data Collection
The Apteco Top 10 highlights the worst offenders, but the problem is systemic. Consider:
-
Fitness & Health Apps: Track steps, heart rate, sleep patterns, menstrual cycles, diet – incredibly sensitive health data often shared with third parties or used for targeted advertising (e.g., weight loss supplements, fitness gear).
-
Dating Apps: Collect sexual orientation, preferences, location data, personal messages, photos. Data breaches or misuse here can be devastating.
-
“Free” Games: Often riddled with ad SDKs harvesting location, identifiers, and usage data. In-app purchases and behavioral tracking are key.
-
Weather Apps: Seemingly innocuous, but many request precise location constantly and are notorious for selling this highly valuable data.
-
Keyboard Apps: Can log everything you type, including passwords and sensitive messages.
-
SDKs (Software Development Kits): The hidden enablers. Even a simple app might include Facebook’s SDK, Google’s Firebase, or numerous ad/analytics SDKs, silently funneling your data back to these giants and other third parties, regardless of the host app’s own policies.
The Illusion of Consent: Dark Patterns & Permission Fatigue
How do these apps get away with collecting so much? It’s rarely through informed, enthusiastic user consent. Instead, they leverage:
-
Dark Patterns: Deceptive design tricks. Think: “Agree to All” buttons brightly colored and prominent, while “Customize Settings” is buried in tiny grey text. Forcing consent for non-essential features to use the core app. Vague or overly broad permission requests (“Improve user experience”).
-
Permission Fatigue: Users are bombarded with complex privacy policies and permission requests. Exhaustion and the desire to just use the app lead to reflexive clicking “Allow.”
-
Bundled Permissions: Requesting access to contacts when it’s only needed for a minor “find friends” feature, but the permission grants access to the entire address book.
-
Ongoing Surveillance: Permissions granted once (like location “Always”) often mean continuous collection with no further prompts, long after the initial need has passed.
-
Lack of Meaningful Alternatives: For many essential services (like banking or municipal apps) or dominant social platforms, there are no real privacy-respecting alternatives, forcing users into a “take it or leave it” scenario.
Taking Back Control: Practical Steps for the Privacy-Conscious User (Beyond Just Deleting Apps)
Deleting the top offenders might be ideal, but it’s often unrealistic. Here’s a layered defense strategy:
-
Ruthless Permission Auditing (iOS & Android):
-
Go Deep: Don’t just glance. Go to Settings > Privacy & Security (iOS) or Settings > Apps > Permissions (Android). Review every permission (Location, Camera, Microphone, Contacts, Photos, etc.) for every app.
-
The “Why” Test: For each permission, ask: “Does this app absolutely need this access to function?” Does a weather app need precise location always, or would coarse location while using suffice? Does a note-taking app need your contacts? Default to “Never” or “Ask Every Time.” For Location, ALWAYS choose “While Using the App” unless you have a compelling, ongoing reason for “Always” (like a trusted navigation app during a journey). Use “Precise Location: Off” whenever possible.
-
Schedule Audits: Do this quarterly. Apps update and permissions can change.
-
-
Leverage Platform Privacy Tools:
-
Apple App Tracking Transparency (ATT): This is CRUCIAL. Go to Settings > Privacy & Security > Tracking. DISABLE “Allow Apps to Request to Track” globally. This blocks apps from accessing the IDFA (Identifier for Advertisers) for cross-app tracking. If you leave it on, say “Ask App Not to Track” for every single request. Be relentless.
-
Apple Privacy Report (Safari): See which trackers are being blocked on websites you visit (Settings > Safari > Privacy Report). Reveals the hidden ecosystem.
-
Android Privacy Dashboard (Android 12+): See a timeline of which apps accessed sensitive permissions (Location, Camera, Mic) and when. A powerful visibility tool. Use “Privacy Indicators” for mic/camera access.
-
Google Ad Settings: Manage your ad personalization profile (though this only affects Google’s own ads, not data collection). Consider resetting your Advertising ID periodically (Settings > Privacy > Ads on Android).
-
-
Limit Ad Tracking & Reset Identifiers:
-
iOS: Settings > Privacy & Security > Tracking > Disable “Allow Apps to Request to Track.” Also, Settings > Privacy & Security > Apple Advertising > Turn Off Personalized Ads (limits Apple’s own targeting).
-
Android: Settings > Privacy > Ads > Tap “Delete advertising ID” and/or “Opt out of Ads Personalization.” Do this monthly.
-
-
Scrutinize Privacy Labels & Policies (Before Downloading!):
-
Apple App Store: ALWAYS check the “App Privacy” section before installing. Look for high numbers in “Data Linked to You.” Be wary of apps collecting Sensitive Info, Precise Location Always, Contacts, or User Content without clear justification.
-
Read the Fine(ish) Print: Skim the privacy policy. Look for sections on “Data Sharing,” “Third Parties,” and “Data Retention.” Avoid apps with vague language or excessive sharing.
-
-
Mitigate In-App Browsing Risks:
-
NEVER browse sensitive sites (banking, healthcare, anything private) within Facebook, Instagram, X, or Pinterest’s in-app browsers. ALWAYS open links in your default browser (Safari, Chrome, Firefox). Better yet, use a browser with strong tracker blocking (Firefox Focus, Brave, Safari with content blockers).
-
-
Embrace Privacy-Focused Alternatives:
-
Search: DuckDuckGo or Startpage instead of Google.
-
Email: ProtonMail or Tutanota instead of Gmail.
-
Messaging: Signal or Session instead of WhatsApp/Facebook Messenger (Note: WhatsApp is owned by Meta; while it has E2EE, metadata is collected).
-
Browser: Firefox (with strict tracking protection/uBlock Origin) or Brave.
-
Maps: Organic Maps or OsmAnd (OpenStreetMap based) for offline, privacy-focused navigation. Use Apple Maps with “Precise Location: Off” over Google Maps.
-
Social: Consider if you truly need all platforms. Explore decentralized options like Mastodon (though user base is smaller).
-
-
Strengthen Your Foundational Security:
-
Strong, Unique Passwords & a Password Manager: Essential to prevent account takeovers that expose all your data. Use Bitwarden, 1Password, or iCloud Keychain.
-
Two-Factor Authentication (2FA): MANDATORY for email, financial, and social media accounts. Use app-based (Authy, Google Authenticator) or hardware keys (YubiKey) over SMS if possible.
-
Regular Updates: Keep your phone OS and all apps updated to patch security vulnerabilities that could be exploited to steal data.
-
VPN (Use Judiciously): A VPN encrypts traffic between your device and the VPN server, hiding your IP from the websites/apps you use and your ISP. However, it does not stop the app itself from collecting and sending your data (like location, identifiers, usage data) to its own servers. Choose reputable, no-logs VPNs if you use one (e.g., ProtonVPN, Mullvad). Don’t trust free VPNs.
-
-
The Nuclear Options (When Necessary):
-
Delete Unnecessary Apps: Be brutal. If you haven’t used an app in 3 months, delete it. Reduce your attack surface and data footprint.
-
Use Web Versions: Access Facebook, Instagram, Twitter, etc., via your browser (with strong ad/tracker blockers) instead of the app. This often limits background data collection and location access. Log out when done.
-
Dedicated Devices/Separation: Consider using a separate device or profile for highly sensitive activities (e.g., financial management) completely isolated from social media and games.
-
The Future of Data Privacy: Regulation, Resistance, and Responsibility
The Apteco report underscores an ongoing battle. While regulations like GDPR (Europe) and CCPA/CPRA (California) have pushed for more transparency and user rights (access, deletion, opt-out), enforcement remains challenging against tech giants with vast resources. Loopholes and the rapid pace of technological change (like AI-driven inference) often outpace legislation.
-
The Role of Legislation: We need stronger, globally harmonized laws with real teeth: banning certain types of data collection (like precise location always), prohibiting dark patterns, requiring true opt-in for sensitive data, limiting data retention periods, and imposing significant fines for violations. The concept of “data minimization” (collecting only what’s strictly necessary) needs to be enforced.
-
Technological Solutions: Privacy-enhancing technologies (PETs) like differential privacy (adding statistical noise to datasets), federated learning (training AI on-device without sharing raw data), and decentralized identity models hold promise but need wider adoption and integration by platforms.
-
User Awareness & Demand: Continued pressure from informed users demanding better privacy practices is essential. Supporting privacy-focused companies and technologies helps shift the market.
-
Corporate Accountability: Tech giants must move beyond performative privacy measures and genuinely embrace “Privacy by Design” – building privacy into their products from the ground up, not as an afterthought. Transparency needs to be meaningful, not just compliance checkbox exercises.
Bottom-Line: Knowledge is Power, Action is Protection
The Apteco Top 10 list is a stark reminder: our digital lives are under constant, sophisticated surveillance by the very tools we rely on. Meta’s dominance is alarming, but the ecosystem of data extraction is vast and interconnected. The sensitive “Data Linked to You” collected paints an intimate, often unsettlingly accurate, portrait of who we are, where we go, what we do, and what we think.
Understanding this is the first crucial step. You are not powerless. By becoming ruthlessly selective with app permissions, leveraging platform privacy controls like ATT, scrutinizing privacy labels, seeking out alternatives, and practicing strong foundational security, you can significantly reduce your digital footprint and reclaim a measure of control. It requires vigilance and effort – the price of privacy in the 21st century.
This isn’t about paranoia; it’s about fundamental rights. Your personal data is valuable. It’s your digital identity, your autonomy, and your vulnerability. Treat it with the care it deserves. Demand better from the platforms you use. The choices you make about your data today shape the privacy landscape of tomorrow. Choose wisely, and choose actively. Your digital self depends on it.